I’m sure that you have had this scenario at least once: you download a file from the internet and try to run it and it doesn’t work fine. If it is a CHM file, the help file doesn’t open the content:
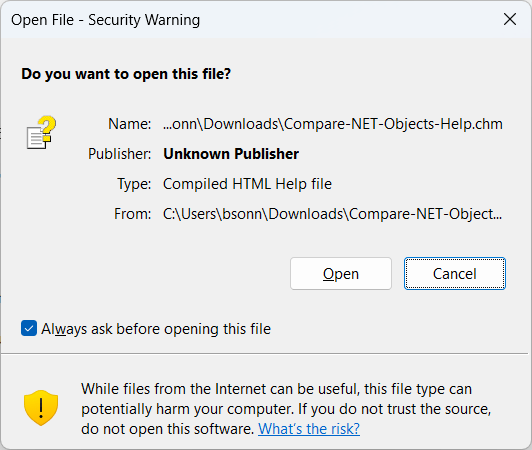
If it’s an executable, it will show a message telling you that you got it from an unreliable source or, even worse, it stays there and does nothing. A client of mine set me a zip with some files to install. I downloaded the zip, unzipped it and tried to run and nothing happened. The only thing I could do is to open Task Manager and kill the Explorer process.
This is caused by a mechanism Windows has to lock files that come from the internet and can harm your computer. If it is a zipped file and you unzip it with Explorer, all extracted files will be protected with this mechanism. If you right click the file in Explorer, select Properties and check on the “Unlock” box, everything runs fine. The file is unlocked.
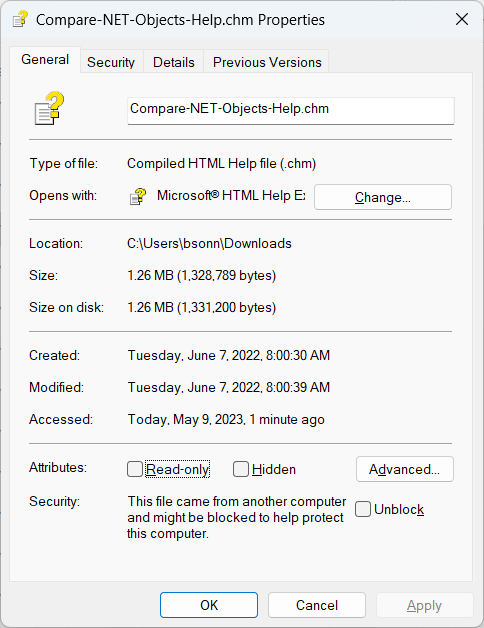
But what is this protection mechanism and how can we check if the file is protected and unprotect it?
The mechanism used is called “Alternate Data Streams” (ADS), and it’s a way that NTFS has to add extra data in a file. This data is not shown when you open a file and is size is not added to the total file size, but the data is there, hidden and taking disk space. If you open a command line prompt window and do a Dir /R command, you can see these alternate streams:
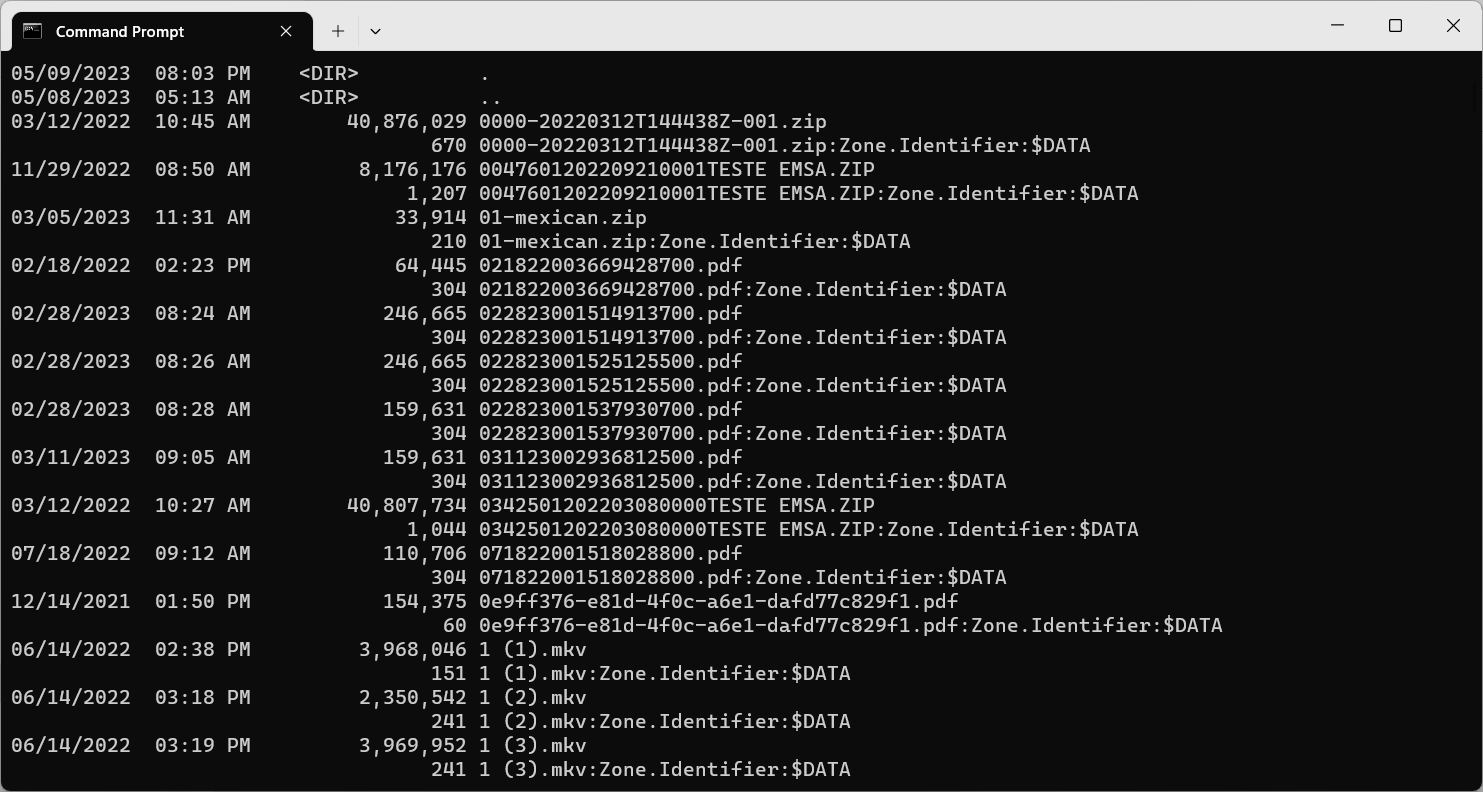
In the image above, you can see two lines for each file. The first one is the “real” file, and the second one is the “hidden” file. You can see that the “hidden” file has the same name of the “real” file and a complement after the colon. The Zone.Identifier:$DATA is the alternate stream for the file. It may have any name and can have any size (it can even be larger than the “real” file) and it’s a very effective way to hide information – if you open a file, you won’t see any trace of the alternate data stream. But, with great power comes great responsibility, and that can also be used for evil purposes – it can hide things the user is not aware and would not want in his computer.
For our blocked files, we know that they have a ADS, named Zone.Identifier. But what’s in the files? To show the contents of an ADS, you cannot use the normal tools. You can use Powershell to open them. For example, if you open a Powershell command line (se Window+X, then select “Windows Powershell”, you can type
Get-Content -Path .\Web_Servers_Succinctly.pdf -Stream Zone.Identifier
And it will show the contents of the file:
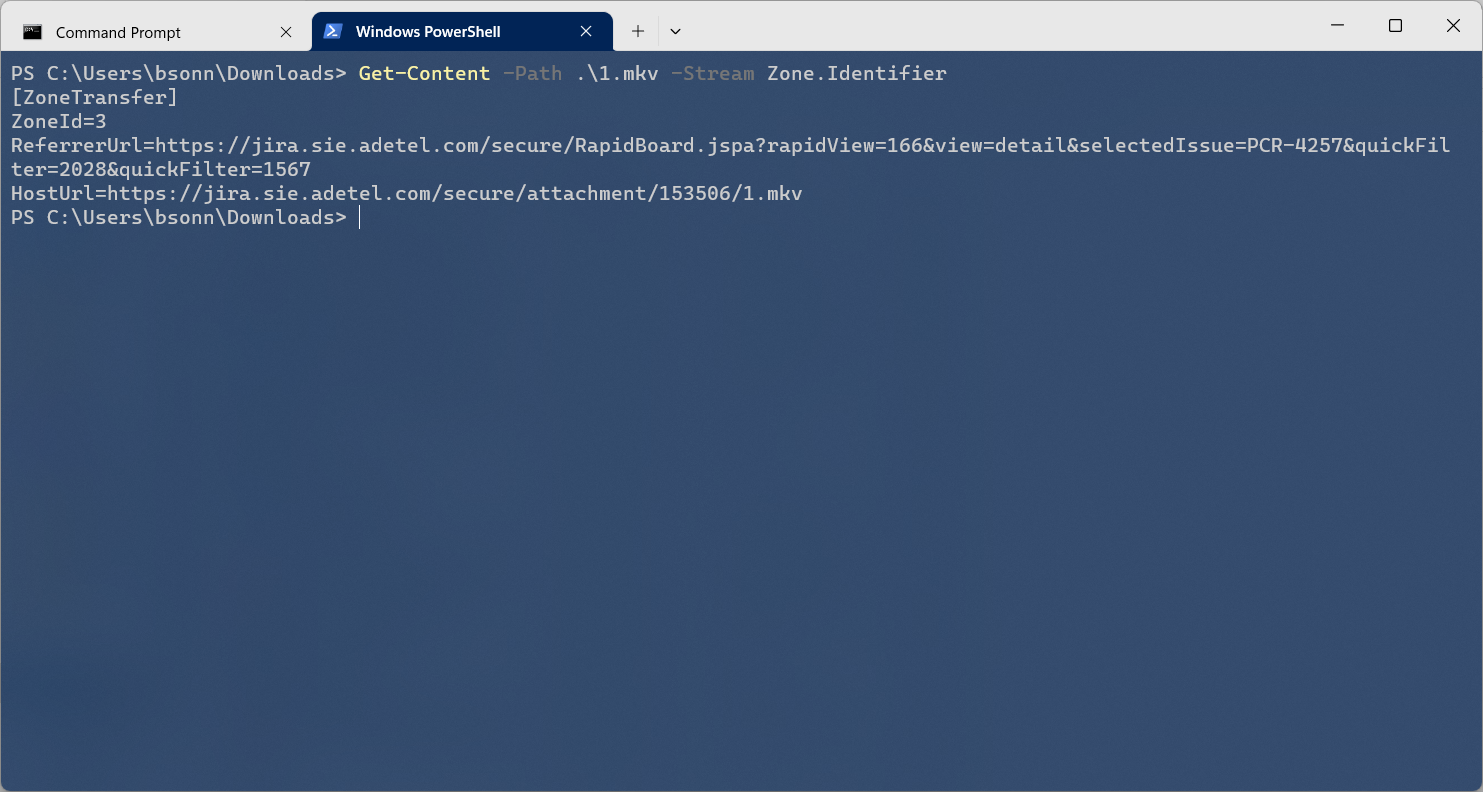
We can see that this file was transferred from Zone=3. From here we can see that 3 is URLZONE_INTERNET, the file came from the internet. So that’s what is blocking the file. It we unblock the file, we are removing the stream:
Manipulating ADSs with C#
Now we know the mechanism behind Windows protection and we can create a C# program that unblocks all files in a directory. There is no API to access file streams in .NET, so you must resort to Win32 P/Invoke. The functions NtfsFindFirstStream and NtfsFindNextStream enumerate all streams in a file. DeleteFile will delete a stream, and CreateFile will create and add the stream.
Fortunately, we don’t have to work with this functions, as a brave developer has created a library to handle ADS in .NET (https://github.com/RichardD2/NTFS-Streams) and we can add it from Nuget. We will create a program to list, show contents or delete alternate streams with C#.
In Visual Studio, create a new Console application. Right click in the References node and select Manage Nuget Packages. There, install Trinet.Core.IO.Ntfs.

Then, in Program.cs, we will start to create our program:
static void Main(string[] args)
{
if (args.Length == 0)
{
Console.WriteLine("usage: adsviewer -(l|s|d) [streamname]");
return;
}
var selSwitch = ProcessSwitches(args);
if (selSwitch == null)
return;
var parameters = args.Where(a => !a.StartsWith("-"));
string fileName = ".";
if (parameters.Count() > 0)
fileName = parameters.First();
var streamName = parameters.Skip(1).FirstOrDefault();
if (File.Exists(fileName))
ProcessFile(fileName, streamName, selSwitch);
else if (Directory.Exists(fileName))
foreach (var file in Directory.GetFiles(fileName))
ProcessFile(file, streamName, selSwitch);
else
{
Console.WriteLine("error: file/folder does not exist");
return;
}
}
Initially, we’ve checked if the user passed any parameters. If not, we show the usage help. Then, we process the switch (the option with a hiphen), that can be a “l” (to list the stream names), a “s” (to show the content of the streams or a “d” (to delete the streams.
Then, we get the file or folder name and the stream name. If the user didn’t pass any file name, we admit he wants to process all the streams in all files in the current directory. If he passes a name, we check if it’s a file or a folder. If it’s a folder, we will process all files in that folder.
If the user passes a stream name, we will only process that stream. If he doesn’t pass a name, we will process all streams in the file.
ProcessSwitches checks the passed switch and sees if its valid:
private static string ProcessSwitches(string[] args)
{
var switches = args.Where(a => a.StartsWith("-"));
if (switches.Count() > 1)
{
Console.WriteLine("error: you can use only one switch at a time (-l, -s, -d)");
return null;
}
var selSwitch = switches.Count() == 0 ? "l" : switches.First().Substring(1);
if (!"lsd".Contains(selSwitch))
{
Console.WriteLine("error: valid switches: -l(ist), -s(how contents), -d(elete)");
return null;
}
return selSwitch;
}
ProcessFile will process one file. If the user passed a directory name, we enumerate all files in the directory and call ProcessFile for each file.
private static void ProcessFile(string fileName, string streamName, string selSwitch)
{
switch (selSwitch)
{
case "l":
ListStreams(fileName);
break;
case "s":
ShowContents(fileName, streamName);
break;
case "d":
DeleteStream(fileName, streamName);
break;
}
}
Then, we have three kind of processing: if the user wants to list the names, we call ListStreams:
private static void ListStreams(string fileName)
{
FileInfo file = new FileInfo(fileName);
Console.WriteLine($"{file.Name} - {file.Length:n0}");
foreach (AlternateDataStreamInfo s in file.ListAlternateDataStreams())
Console.WriteLine($" {s.Name} - {s.Size:n0}");
}
It will enumerate all streams and list their names and sizes. The second processing is to show the contents, in ShowContents:
private static void ShowContents(string fileName, string streamName)
{
FileInfo file = new FileInfo(fileName);
Console.WriteLine($"{file.Name} - {file.Length:n0}");
if (!string.IsNullOrWhiteSpace(streamName) && file.AlternateDataStreamExists(streamName))
{
AlternateDataStreamInfo s = file.GetAlternateDataStream(streamName, FileMode.Open);
ShowContentsOfStream(file, s);
}
else if (string.IsNullOrWhiteSpace(streamName))
foreach (AlternateDataStreamInfo s in file.ListAlternateDataStreams())
ShowContentsOfStream(file, s);
}
If the user passed a name of a valid stream, it will show its contents. If it has not passed a name, the program will enumerate all streams and show the contents for them all. The ShowContentsOfStream method is:
private static void ShowContentsOfStream(FileInfo file, AlternateDataStreamInfo s)
{
Console.WriteLine($" {s.Name}");
using (TextReader reader = s.OpenText())
{
Console.WriteLine(reader.ReadToEnd());
}
}
Finally, the third kind of processing is to delete the streams. For that, we use the DeleteStreams method:
private static void DeleteStream(string fileName, string streamName)
{
FileInfo file = new FileInfo(fileName);
Console.WriteLine($"{file.Name} - {file.Length:n0}");
if (!string.IsNullOrWhiteSpace(streamName) && file.AlternateDataStreamExists(streamName))
{
file.DeleteAlternateDataStream(streamName);
Console.WriteLine($" {streamName} deleted");
}
else if (string.IsNullOrWhiteSpace(streamName))
foreach (AlternateDataStreamInfo s in file.ListAlternateDataStreams())
{
s.Delete();
Console.WriteLine($" {s.Name} deleted");
}
}
If the user passed a valid stream name, the program will delete that stream. If he hasn’t passed a name, the program will delete all streams in the file.
That way, we arrived at the end of our program.
Conclusions
ADSs are used in many ways, to add extra data to a file. Although there are legitimate ways to use them, sometimes, that can be used to store harmful data. We have developed a tool that can list all ADSs in a file, show their contents or delete them. With it, you can analyze the data that is attached to your file and decide what to do with it. Next time you get something that came from the internet and is blocked, you can easily unblock it with this tool.
The full source code is in http://github.com/bsonnino/ADSViewer
